Partner FAQ:
What is being announced?
We are pleased to announce the launch of ThreatSync+ NDR and WatchGuard Compliance Reporting. These products are based on the technology acquired from CyGlass in September of 2023. The marketing release of the product: June 25. GA release: June 28.
Why are we adding ThreatSync+ to the NDR name?
WatchGuard acquired CyGlass back in September of 2023. With that purchase, we acquired an advanced unsupervised and semi-supervised layered neural network AI engine that can process billions of data flows to find risks and threats across any environment. That AI engine is the heart of the new ThreatSync+ family of products. Beginning with network flow data in ThreatSync+ NDR, WatchGuard will add new data inputs into the ThreatSync+ AI engine and deliver world-class threat detection and response solutions for all threat surfaces across an organization. ThreatSync+ NDR is just the beginning. Future ThreatSync+ products will include Cloud platforms, endpoints, identity directories, secure edge devices, and more.
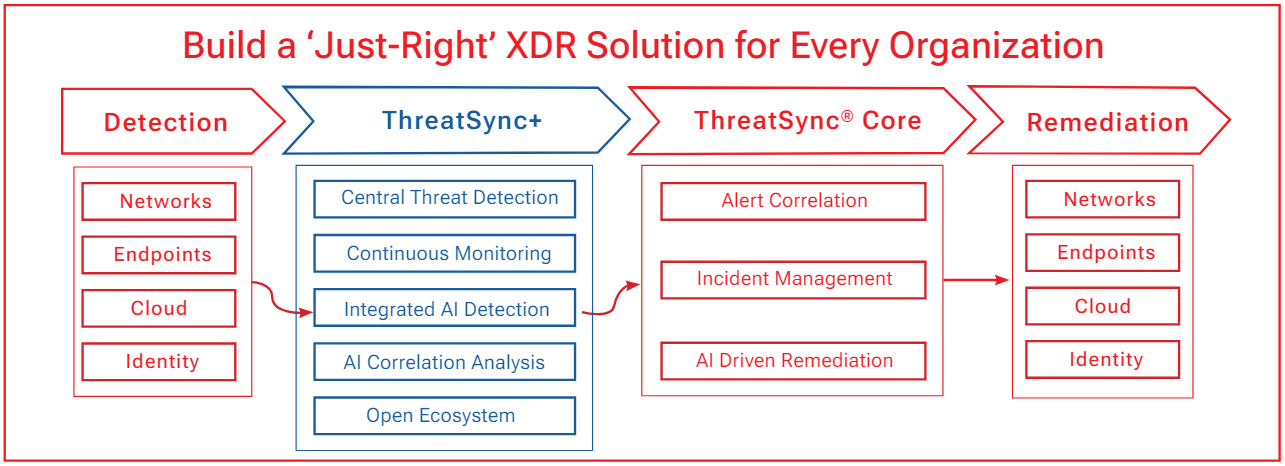
How does ThreatSync+ expand on WatchGuard's XDR strategy?
ThreatSync, as we know it today, will continue to be a platform capability that delivers the foundation of WatchGuard's XDR strategy, most notably providing the unified remediation and response engine necessary for XDR capabilities. The ThreatSync+ AI engine will layer on advanced AI-based threat detection and analysis and open the door to third-party participation to grow and expand WatchGuard's XDR offering, creating an Open XDR solution that can compete and win against any existing XDR tool in the market. WatchGuard customers and partners get the foundational XDR engine – which we will call the ThreatSync Core functionality – whenever they purchase qualifying products without any additional license purchase. They can add ThreatSync+ licenses to customize their XDR solution to fit their unique needs, beginning with our ThreatSync+ NDR license now, and the ThreatSync+ SaaS license later in 2024. ThreatSync Core and ThreatSync+ NDR work seamlessly for powerful XDR functionality.
What does ThreatSync+ NDR do?
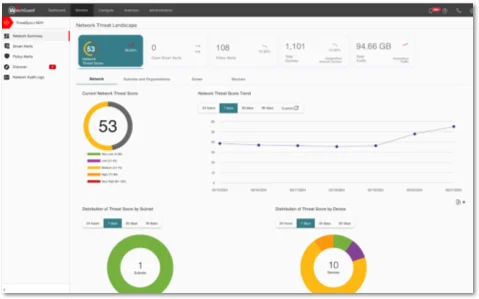
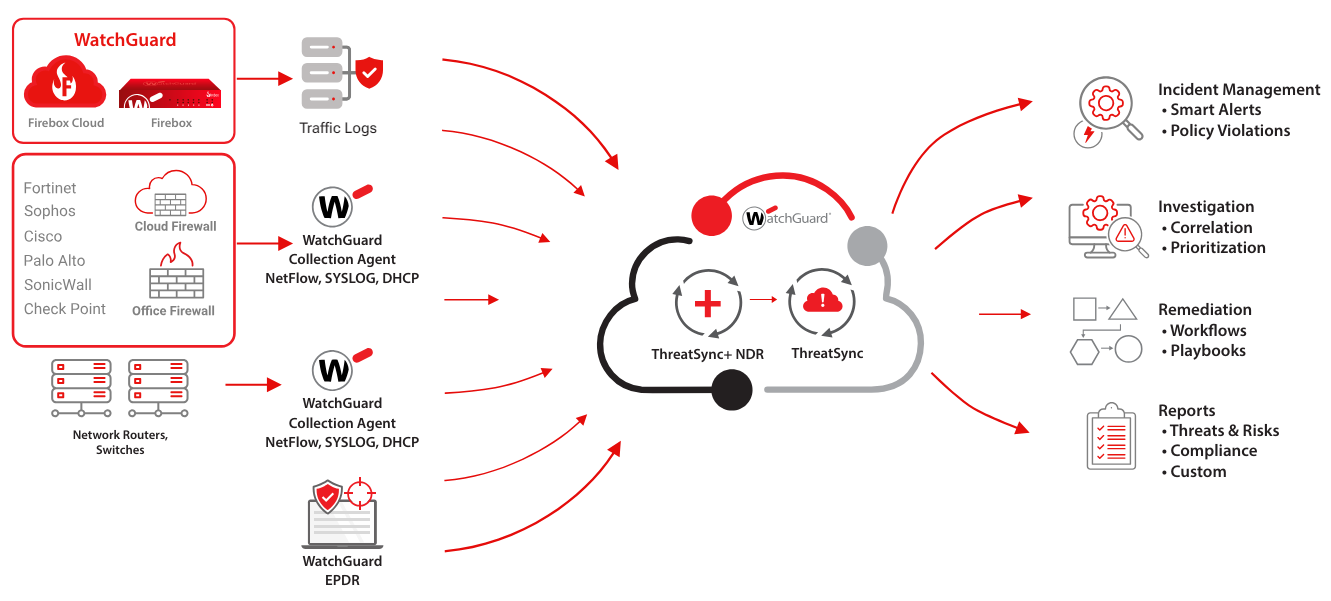
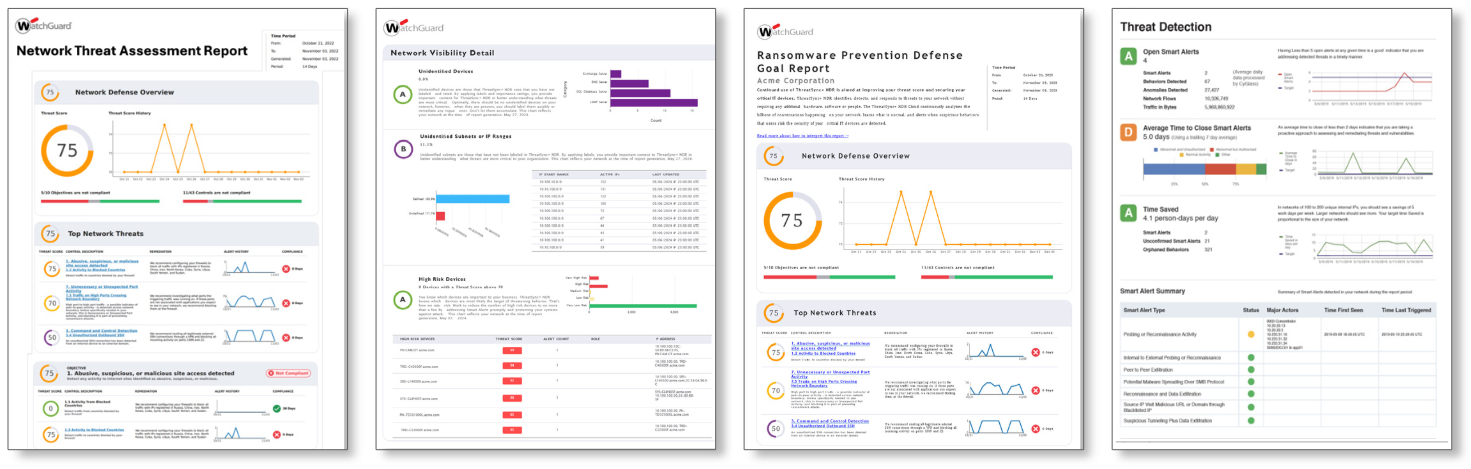
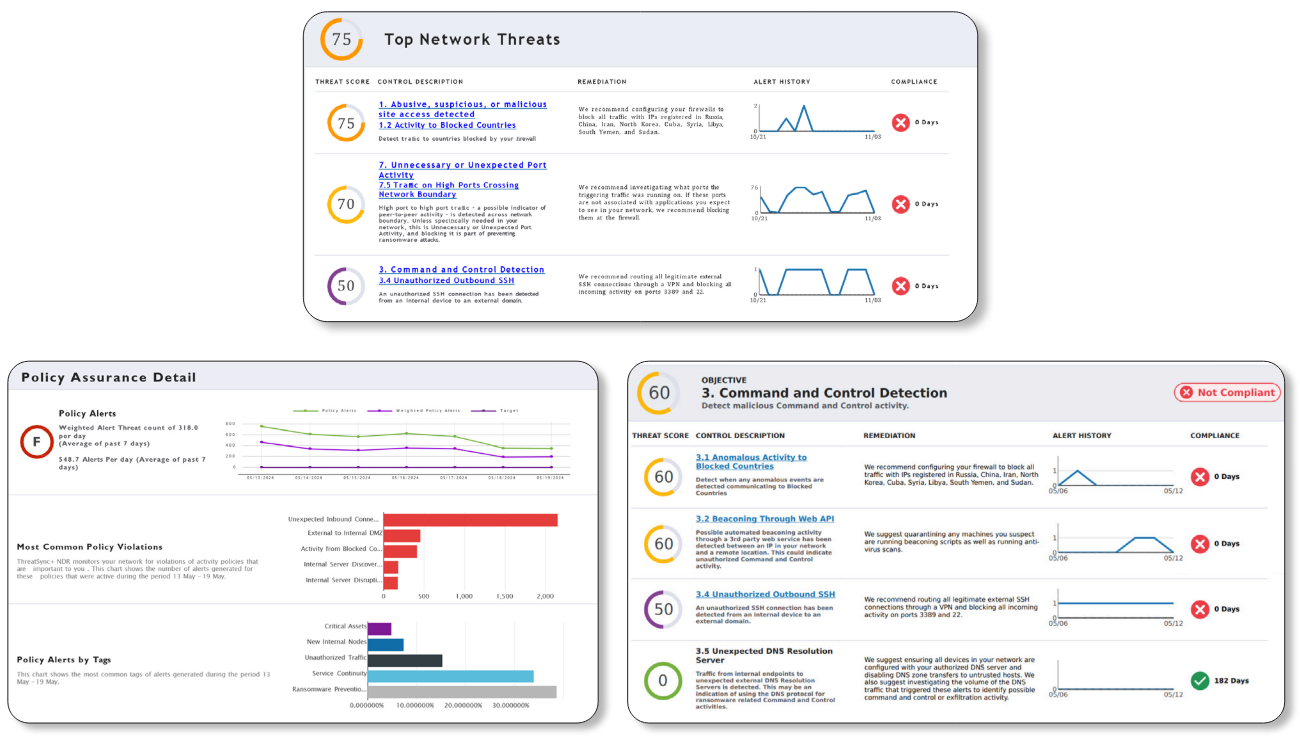
ThreatSync+ NDR is a network detection and response solution that uses the ThreatSync+ AI engine to continuously monitor all north/south and east/west traffic flows for risks and threats. ThreatSync+ NDR will gather network traffic flows from firewalls, routers, and switches and build AI-defined models of what is normal and anomalous. Working with an integrated policy engine, the AI engine will correlate and present the anomalies as risk-scored and prioritized incidents. Cyber defenders will see a short, prioritized view of the risks and threats in a series of dashboards that display those risks and threats in terms of location, devices, users, and timelines. ThreatSync+ NDR can take billions of network conversations and find in them the five or six critical items cyber defenders must focus on to protect their organizations, along with guidance on how to mitigate them.
What makes ThreatSync+ NDR different and unique?
ThreatSync+ NDR differentiators include:
- ThreatSync+ NDR was designed for our customers, and businesses who operate with smaller IT teams and limited cybersecurity resources. Where other NDR tools are complex to operate, require a full security operations center to truly utilize, and force the deployment of multiple hardware clusters, ThreatSync+ NDR operates in the WatchGuard Cloud. It deploys rapidly (in less than an hour per location) and instantly if you are using Firebox firewalls, requires no new on-premises hardware as it utilizes the infrastructure you have, operates as a stand-alone from a SIEM or a SOC, and its simplicity means small IT teams can operate it.
- ThreatSync+ NDR delivers enterprise-class machine learning. It is one of the market's most advanced AI detection engines, cutting through the noise of billions of network flows to surface actionable risks and threats quickly and efficiently. It includes specialized AI models to detect advanced threats like ransomware, vulnerability-based attacks, supply chain attacks and more. It watches continuously, 24x7, looking for the attacks that get through your perimeter defenses.
- ThreatSync+ NDR automates and simplifies continuous monitoring, detection, and remediation. It significantly reduces the workload for small teams. The AI engine does the work for you, and the easy-tounderstand dashboards, guidance, and reporting mean any IT team member can operate the solution.
- ThreatSync+ NDR works seamlessly with WatchGuard Firebox and ThreatSync Core. It also supports thirdparty firewalls like Fortigate and Meraki and industry-standard routers and switches, making it effective in any organization.
What is WatchGuard Compliance Reporting?
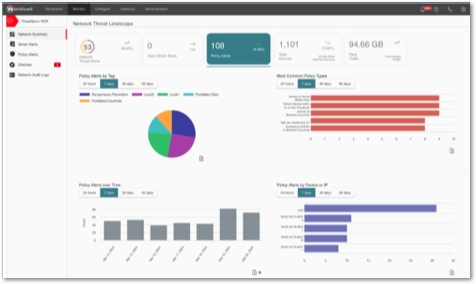
WatchGuard Compliance Reporting is an additional add-on license for organizations that must prove compliance in highly regulated industries. ThreatSync+ NDR includes hundreds of network controls defined by the NIST, ISO, CISA, and Cyber Essential standards. These controls are easily activated at deployment. WatchGuard Compliance Reporting allows IT and compliance teams to activate and report on regulatory laws built from these standards. Compliance reports that come out of the box include FFIEC, NIST-171, CMMC, GPDR, IEEE, and many more. Reports are also easily configured to report in compliance with custom standards imposed by a cyber insurer or industry standards like Motion Picture Association (MPA) compliance or supply chain vendor third-party risk assessments. WatchGuard Compliance Reporting automates the traditionally manual/spreadsheet-driven IT control compliance process.
How is WatchGuard Compliance Reporting different?
Existing NDR and XDR tools do not include a compliance reporting capability. They are separate, expensive, complex tools usually built around a legacy Governance Risk and Compliance product (GRC). At the same time, many of WatchGuard's customers are small and midsize enterprises that must prove compliance with regulatory laws and do not have the resources to deploy GRC types of products. WatchGuard Compliance Reporting fills that gap, delivering a simple-to-use report creation framework and automated report creation, delivering an affordable, efficient compliance reporting solution. WatchGuard Compliance Reporting key selling features include:
- With a click of a button, WatchGuard Compliance Reporting generates regulatory compliance reports automatically to prove adherence to compliance standards.
- Reports are easily created, configured, and modified for new or changing regulatory needs.
- The reports generated by WatchGuard Compliance Reporting provide a comprehensive view of the effectiveness of each control, the risk associated with any failed control, and an overall risk and compliance score for the entire compliance program.
- Working with current and future ThreatSync+ family of products, WatchGuard Compliance Reporting ensures that compliance reports are constantly updated. This continuous compliance process provides auditors with instant visibility.
- Compliance reports for specialized control effectiveness reporting for insurance, vendor third-party risk, and industry oversight trade associations are also easily created and configured as needed.
- There is no limit on how many compliance reports can be created, and the automated structure of the report creation eliminates expensive manual compliance tracking.
Who are these solutions targeting?
ThreatSync+ NDR and WatchGuard Compliance Reporting are designed for businesses of any size that operate with lean IT teams and limited cybersecurity skills/resources. That is often the case for small and midsized businesses a market largely underserved by vendors selling NDR, XDR, and compliance products. ThreatSync+ NDR is compelling for organizations as small as 50 employees to organizations as large as 30,000.
How are these solutions being packaged?
The June 28 release includes two new SKUs. ThreatSync+ NDR, the first of the ThreatSync+ family of solutions, includes an advanced AI detection engine, specialized AI models to detect advanced network and device risks and threats, hundreds of industry-standard best practice network controls, and the ability to ingest data from Firebox and third-party firewalls as well as industry-standard routers and switches. The second new SKU is WatchGuard Compliance Reporting. WatchGuard Compliance Reporting is an add-on solution to the ThreatSync+ NDR solution and is the compliance reporting engine that overlays the entire ThreatSync+ family.
Is ThreatSync and ThreatSync+ included in the WatchGuard TSS bundle?
The ThreatSync Core capabilities remain a part of the WatchGuard TSS bundle, just like it is today. All ThreatSync+ solutions, including ThreatSync+ NDR, are activated with an additional license that customers must purchase. This approach is because WatchGuard focuses on serving all organizations. Some customers need core XDR capabilities but not the more advanced capabilities in the ThreatSync+ solution. The packaging models allow every organization to utilize the incident correlation and response capabilities in ThreatSync Core along with the detection capabilities of the endpoint (EPDR) and network (Firebox) that WatchGuard currently offers. Organizations with greater cybersecurity requirements and/or complex hybrid environments can add ThreatSync+ protection levels to protect their environments, building an XDR solution that fits their needs and benefiting from WatchGuard products work seamlessly together.
How are these solutions being licensed?
ThreatSync+ NDR and WatchGuard Compliance Reporting are priced per user per year. Each per-user license includes up to two devices, e.g., the user's laptop and mobile device. IoT devices are priced at two IoT devices per license and utilize a per-user SKU. As the number of devices and volume of dataflows constantly change, per user is the easiest, most accurate, and fairest pricing model for these solutions. A license can be purchased on a one- or three-year basis, which includes discounts for multi-year purchases. Discounts are also available based on volume. Please refer to the most current WatchGuard price list for specific numbers.
What does ThreatSync+ NDR protect?
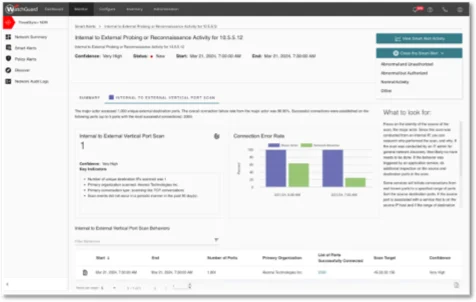
ThreatSync+ NDR protects on-premises networks from attack. It is especially good at finding attacks that have bypassed perimeter defenses, including ransomware, vulnerability, and supply chain attacks. It seems that every week, a new major attack occurs. These organizations have firewalls and some type of endpoint defense; still, the attacks get through. This is because some attacks find gaps, like new or unpatched vulnerabilities, to bypass these defenses, or the attacks are more advanced than the existing defenses. ThreatSync+ NDR watches for attacks as they unfold in the network. The attackers cannot see the NDR tool, but the NDR tool uses AI to search out the attackers' actions buried in the network traffic. The attacker cannot hide because they must use the network to expand their attack. That means NDR is uniquely capable of detecting unfolding attack stages, including command and control calls, lateral movement in the network, reconnaissance scans done on networks and subnets, datastaging movement in the network, malware and encryption packages being deployed in the network, and data exfiltration.
If NDR is so powerful, what is it not used by every organization?
NDR is used by almost every large enterprise with a SOC. However, legacy NDR vendors rely on complex hardware and taps to capture and analyze network traffic. Other organizations want to deploy NDR but cannot, due to resource constraints. ThreatSync+ NDR is different. It does not require any new hardware and operates in the WatchGuard Cloud. That means it costs less to deploy and operate. It is one of the few NDR solutions that can be successfully deployed and operated by organizations with lean IT teams.
What Type of AI is in ThreatSync+ NDR?
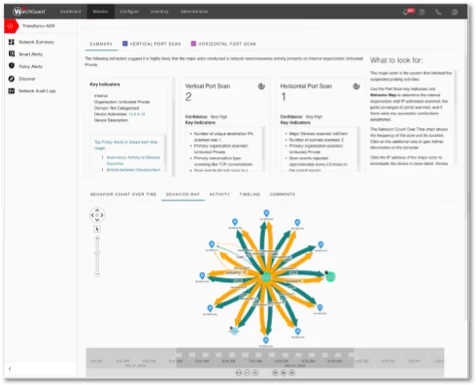
The ThreatSync+ AI engine is a modern unsupervised and semi-supervised flow-focused machine learning engine that utilizes multiple math theorems and statistical models, depending on the data, to create continuous baselines that define "normal" operations and anomalous activities. A second set of machine-learning models, working in conjunction with policies, looks specifically at the anomalies to determine if they are threats. This duallayered "neural network" approach is unique and essential because the data sets are so large that no human or policy-based tool can effectively utilize the information hidden within. At the same time, the AI needs additional context about the environment to determine what is risky or threatening versus what is simply different. The result is that the ThreatSync+ AI engine can take millions, even billions, of data flows and boil them down into a risk-prioritized view of what needs attention and what to do about it.
Why do customers deploy an NDR alongside a firewall solution?
Firewalls are policy-based enforcement systems with file inspection to look for malicious payloads. They effectively manage port and protocol traffic and stop known threats when configured correctly. ThreatSync+ NDR is a threat detection system that adds another layer of intelligence (AI) to the firewall's policy and UTM capabilities. ThreatSync+ NDR deeply analyzes network traffic from firewalls and network flows through routers and switches to see risks and threats beyond what's possible with firewall inspection alone, including:
- North/south traffic and open-port threats that a firewall may miss due to a misconfigured policy or a new or changing threat.
- East/west traffic risks and threats, including compromised applications (e.g., SolarWinds), a compromised user account when MFA is not in place, and a compromised endpoint missed or not covered by the local EDR defense (in memory attack, compromised user attack, application compromise, unprotected, new, or rogue device with no EDR deployed).
In addition to improving visibility into risks and threats in the network - north/south, east/west, NDR also detects and defines all devices operating on the network and alerts when new devices appear.
Mean time to detect (MTTD) is dramatically reduced with ThreatSync+ NDR. Dwell times for attacks run between 15 and 90 days, but an attack like ransomware needs less than five days to complete its mission. ThreatSync+ NDR, continuously watching network traffic, can detect the attack missed by other sensors. Attacks create anomalous traffic that NDR will quickly detect and alert on. Dwell times drop to hours, meaning attacks can be stopped before damage is done.
Who are the key competitors in the NDR market?
There are many competitors in the NDR market. Most are legacy vendors who focus solely on selling to large enterprises. These include Fidelis, Vectra, ExtraHop, and Plixer, and they will rarely be found in our target market. If you find a partner who is reselling one of these legacy players and the partner targets the SME market, go after that account, as the value of ThreatSync+ NDR will be immediately apparent.
The second set of competitors are the stack vendors – Cisco, Fortinet, Sophos, and Microsoft. Cisco, Fortinet, and Sophos acquired smaller legacy hardware vendors and brought these products to market within their security tool stack. Their NDR solutions are hardware-based, deployed locally in the legacy model, and require significant integration work to get them to work with anything but the vendor's stack – they are closed solutions. Microsoft does not offer an NDR solution, but it has NDR capabilities included in the E-5 license. The capabilities are related to network monitoring and work as an MS Sentinel (SIEM) component. The capabilities do not include AI-driven threat detection; it is purely a policy-based view where remediation happens in Sentinel.
DarkTrace will be the most aggressive competitor you will run into in the market. They are focused on NDR sales and have a significant direct selling team. They target mid-market companies with thousands of US and UK customers. Their tool is a hardware-based solution that must be deployed locally with a network tap. It is costly and complex. They tout their AI capabilities, and 20 years ago, they were on the forefront of unsupervised machine learning. Today, they are not. There are customer complaints about false positives and negatives all over the Internet. The requirement for local hardware makes upgrading their AI and software difficult, putting them technically behind our ThreatSync+ engine. They are also universally disliked by partners and customers for their aggressive business practices.
How does our NDR product handle encrypted traffic?
This question will be asked by any cybersecurity professional who has been in the industry for over ten years. In the days before AI was applied to cybersecurity and encrypted traffic was the norm, NDR tools would tap network traffic, open packets, and read the entire traffic body. NDR and DLP (data loss prevention) tools overlapped back then. As more and more traffic became encrypted, Legacy NDR vendors created new ways and more powerful hardware to decrypt and follow the same "packet capture model." This is one reason why so many NDR vendors are floundering after COVID. Shipping big hardware worldwide became a big problem with supply chain failures. Ultimately, the full packet capture and decrypt model is broken, not because you cannot do it; you can with enough hardware and can and still get results in a reasonable amount of time. The issue is the cost and complexity. All the power and all that hardware, not to mention the storage costs, makes this approach only suitable for very large organizations with fully capable security operations centers.
ThreatSync+ NDR takes an entirely different approach. The solution can still capture the full packet, but our AI eliminates the need to look inside the packet. Instead, we look at all the information about the packet (metadata) and the related flow information. With that information, ThreatSync+ AI can determine if the packet is anomalous, how much risk the packet and flow create, and if the packet is related to a specific stage of a cyberattack. This model is cleaner, faster, and much less complex and finds all of the same risks and threats that legacy tools can find. If a partner or prospect does not believe you, show them a sample threat report and tell them to try the solution out. It only takes 40 minutes to deploy – as opposed to the weeks it takes to deploy a legacy NDR tool.
What are the deployment options for ThreatSync+ NDR
ThreatSync+ NDR operates in the WatchGuard Cloud. You simply configure local firewalls, routers, and switches to enable ThreatSync+ NDR to securely capture data flows and logs, as the solution uses the infrastructure and firewall investments the customer has already made. The deployment can be set to capture north/south traffic from Firebox or third-party firewalls or connect to routers and switches to collect east/west network traffic or both. You never have to deploy additional hardware.
Is ThreatSync+ NDR suitable for MSPs?
Yes, ThreatSync+ NDR is a powerful, easy-to-deploy, and high-value solution for MSP partners. The partners can deploy and manage the solution at their customers' sites via the WatchGuard Cloud and ThreatSync+ user management interface. There is no need for the MSP to deploy hardware. The ThreatSync+ UI will enable them to monitor and respond to risks and threats found by the solution, configure and modify control frameworks and policies to align the solution's continuous monitoring capabilities for each individual customer's environment, and create, configure and deliver threat or compliance reports quickly and efficiently. ThreatSync+ NDR, deployed by an MSP, will allow the partner to deliver a higher level of cyber defense for their clients and create new service revenue streams to drive more business.
Will ThreatSync+ NDR be offered as a managed service?
Yes, the work to integrate the solution and train our SOC team on operating ThreatSync+ NDR in conjunction with existing technology needs to be completed. Then there will be announcements about its inclusion in our managed service offering.
How can I request a demo or trial of the NDR product?
To request a demo or trial of ThreatSync+ NDR, please contact us.
Who should I go to with more questions?
For any questions not addressed in this FAQ and other materials related to the launch of ThreatSync+ NDR, please contact us.